As multicloud architectures become increasingly prevalent, maintaining strong security has grown more challenging than ever. This article outlines eight key strategies for businesses looking to protect their cloud systems. Learn how to streamline security governance, minimize blind spots, and secure your environment across diverse cloud platforms for a unified and secure multicloud setup. Establish centralized […]
Blog
Unlock your business’s potential with data dashboards
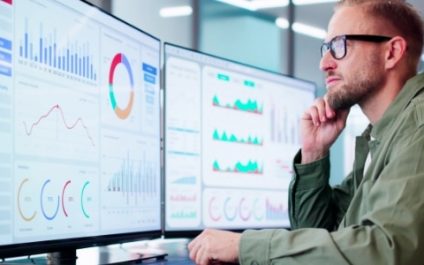
Imagine if you could anticipate your next big sales trend or know which marketing campaign will bring the best return. While they can’t predict the lottery, business dashboards get you close. By visualizing your performance data, these tools help you understand past results and forecast future outcomes more accurately, giving you the insights to be […]
6 Cybersecurity challenges plaguing small businesses

While the media often focuses on cyberattacks against large corporations, small businesses are actually the most vulnerable and frequently targeted. But why have they become prime targets? Here’s a look at the challenges that make it harder for small businesses to keep up with growing cybersecurity demands. False security assumptions Small businesses often face a […]
Data protection with Backup-as-a-Service

The amount of data businesses create is growing at an incredible rate, and protecting it is becoming more challenging. Traditional backup solutions that require expensive hardware and constant maintenance are no longer enough to keep up. Fortunately, there’s a better way. Backup-as-a-Service (BaaS) provides a flexible and cost-effective solution by moving your data protection to […]
Tips to optimize your threat intelligence platform

A good threat intelligence platform (TIP) not only highlights risks but also enables proactive action before they escalate. However, with so much data coming in and numerous features to navigate, using a TIP effectively can be challenging. This guide will walk you through how to prioritize the most relevant intelligence, integrate your TIP seamlessly into […]
Essential strategies to defend your VoIP system against TDoS attacks

Voice over Internet Protocol (VoIP) offers a range of benefits for organizations, including enhanced call quality, greater scalability and mobility, and reduced operational costs. However, it also introduces specific security risks, and among them are telephony denial-of-service (TDoS) attacks. These attacks can significantly disrupt business communications and operations. Gaining a clear understanding of TDoS threats […]
Hybrid clouds: Unlock peak performance and fuel business success

The quest for competitive advantage increasingly leads businesses to reevaluate their IT infrastructure. Hybrid cloud computing offers a compelling answer, providing a versatile and powerful platform that harmonizes on-premises systems with dynamic public cloud services. This synergy is not just about infrastructure; it’s about unlocking new capabilities, fostering innovation, and driving tangible business outcomes. A […]
Stand out with video: Creative strategies to elevate your brand

When done effectively, video marketing captures your customer’s attention and leaves a meaningful impact. By combining solid visuals, concepts, and storytelling, you can create videos that distinguish your brand from competitors. Below are some video marketing ideas and strategies to help your business stand out. Customer testimonial videos The easiest way to take advantage of […]
Essential tips for securing company data in a BYOD environment

Bring your own device (BYOD) policies are transforming workplaces by offering employees the flexibility and convenience of using their preferred personal devices for work. However, each device also presents a potential entry point for cyberthreats. As BYOD becomes the norm, effective security measures are essential to protect data without sacrificing flexibility. Follow these tips for […]
Why protecting your VoIP and communication systems is more important than ever

From cyberattacks to human error, your business communication tools are constantly at risk. This guide explores the critical importance of securing your Voice over Internet Protocol (VoIP) and communication systems, offering practical strategies to protect your team and customers while creating a safer, more reliable environment. The importance of protecting your communication channels today Many […]

